The treacherous trio of APTs: Bears, Pandas, and Chollimas.
APT. Ooo cyber buzz word, anyone up for a game of cyber security bingo? This is the first cyber security blog so I thought it would be a good idea to do a word that pops up everywhere.

APT. Ooo cyber buzz word, anyone up for a game of cyber security bingo? This is the first cyber security blog so I thought it would be a good idea to do a word that pops up everywhere.
Firstly, let's answer the questions of what does APT stand for? An APT is an advanced persistent threat that is typically a nation-state or state-sponsored groups that are known to pursue their targets over long periods of time from months up to years. The APT groups are numbered so for example APT10 which is commonly known as the Chinese APT group, menuPass. The APT numbers are one of many ways that these groups are named, the other main name conversion that I use is Crowdstrike's adversary categorization.
Nation-State-Based Adversaries:
· Bear = Russia
· Buffalo = Vietnam
· Chollima (a mythical winged horse) = North Korea
· Crane = South Korea
· Kitten = Iran
· Leopard = Pakistan
· Panda = China
· Tiger = India
Non-Nation-State Adversaries:
· Jackal = Activist groups
· Spider = Criminal groups
So, the next question is who is targeting Japan out of the long list of groups? Well, Japan must be covered in honey because both kinds of bears, Panda (China) and Bear (Russia) seem to love Japan especially as Japan actually have wild bears. But there is one more group that is licking its lips at the sight of ripe pickings of Japan, and that's Chollima (North Korea), to be specific, it's the North Korea APT group, Lazarus.
North Korea
Lazarus, where have I heard that from? I am not talking about Lazarus from the bible who was the man that Jesus raised from the dead. I am talking about the group of hackers who were attributed to the large-scale breach of Sony Pictures in 2014. That was 6 years ago though so they aren't that important surely? Well, they are important because they still conducting attacks against specific kind of target, which is financial targets like crypto exchanges. There is one thing that I want to point out before anyone starts looking into Lazarus which is there are some organizations that use the name Lazarus Group to refer to any activity attributed to North Korea. Although Lazarus is only one part of the overall North Korea group, the prime agency for North Korea cyber activities is the Reconnaissance General Bureau of North Korea (RGB).
RGB was found in 2009 with objectives of collecting intelligence on Japan, South Korea and the United States. Now anyone who has an interest in cyber warfare or has a MOD/intel background might know about Bureau 121 which is the primary office tasked with disruptive cyber operations. RGB is made up of 8 departments with Bureau 121 being the 8th department. The first noticeable change was in 2003 after the invasion of Iraq by the united states. At the time, the Bureau was seen as a joke but since then, their capability has been growing. Then in 2011, when Kim Jong-un succeeded his father, the Bureau expended their mission to focus on the attacks that we know of nowadays that are based around the theft of intellectual property, financial and political gains. Now with the growth of RGB, came the growth of Lazarus to the point where most companies believe Lazarus has two units: BlueNorOff and AndAriel. BlueNorOff (APT38 or Stardust Chollima) is mainly known as a financially motivated group. And AndAriel (Silent Chollima) is known for target South Korea with a key focus on government, defence, and economic targets.
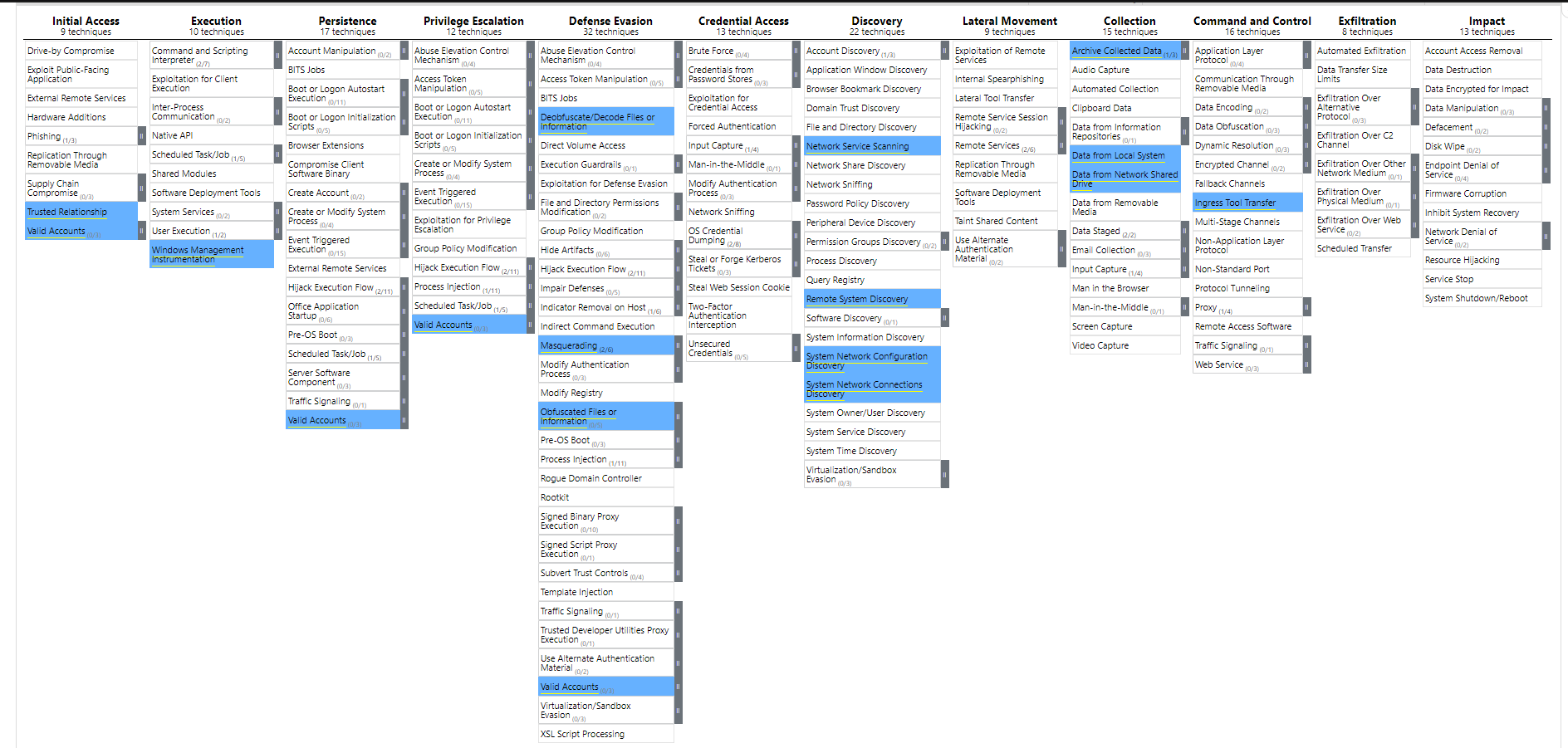
So, we talked about who is who? But what about the attacks? Well, I think the best way I can show everyone what I see in terms of APT groups attacking Japan is using MITRE ATT&CK framework. I started using it last summer during my time in Japan and I have been using it since then. E.g. I used it for one of my university's unit assessments on APT1.
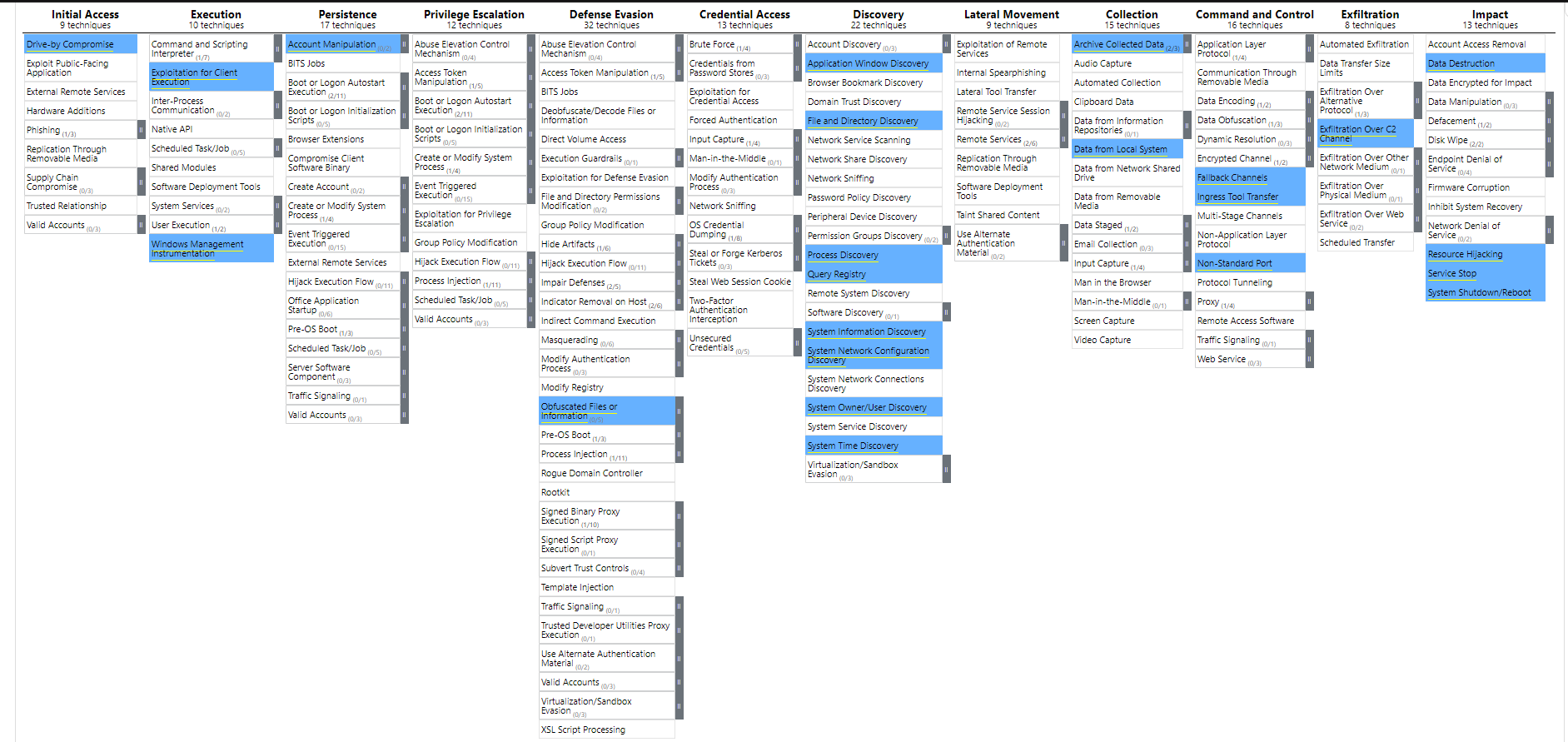
Russia
Two main Russian APT groups that have been known to target Japan are Fancy Bear (APT28) and Cozy Bear (APT29). Fancy Bear has been associated with the Russian military intelligence agency, Glavnoye Razvedyvatelnoye Upravlenie (Chief Intelligence Office) and the Russian government. Recently Fancy Bear has been identified as two GRU units known as Unit 26165 and Unit 74455. Unit 26165 is said to be the unit that carries out core hacking activities and Unit 74455 carries out information operations aimed around information warfare. The operations of these units were confirmed by charges brought against twelve GRU men who were indicted from the two units. Fancy Bear is known for registering domains that closely resemble domains of legitimate organizations that they use to harvest their target's credentials.
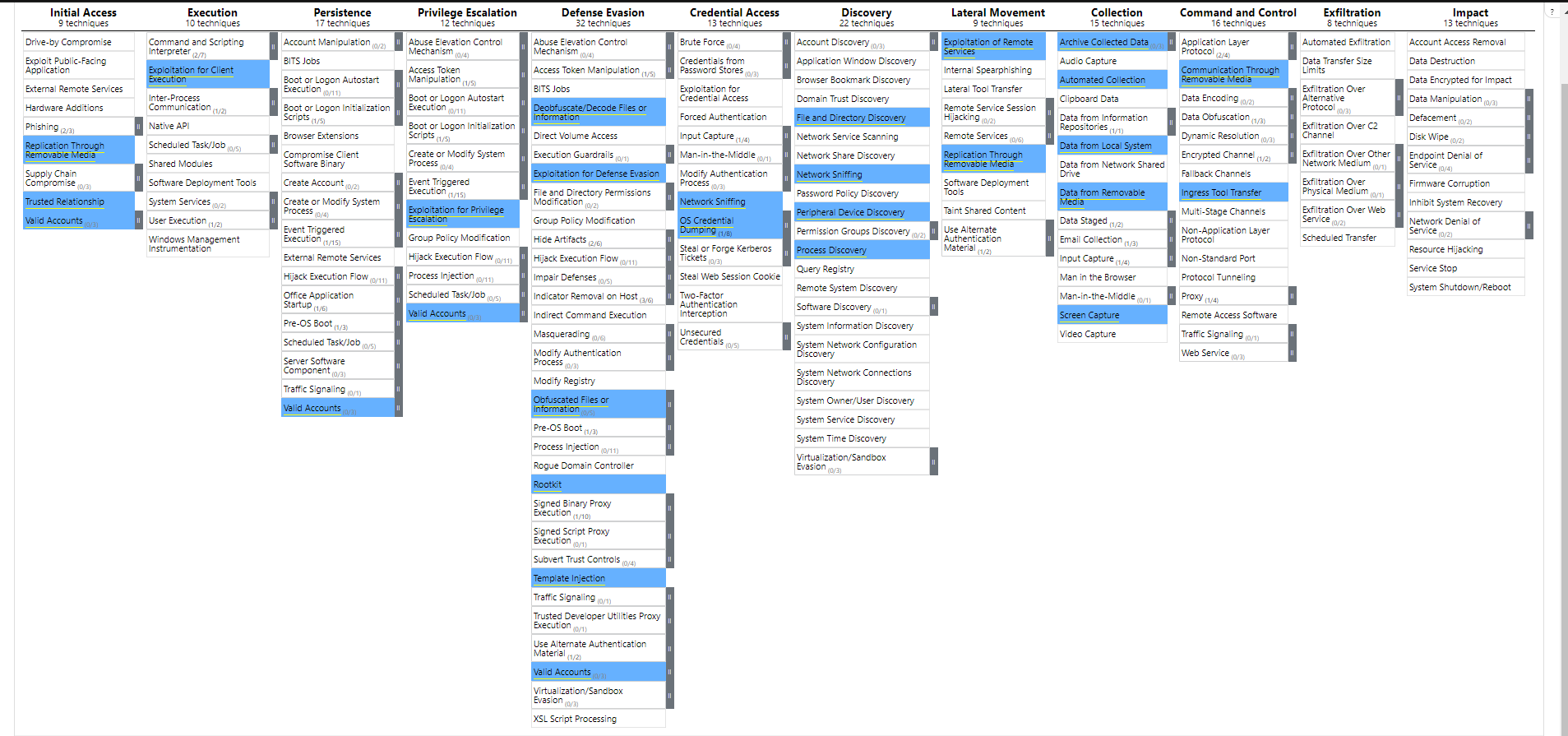
Cozy Bear has been associated with the Russian Foreign Intelligence Service (SVR) but there is also the belief that it could be associated with other intelligence agencies of Russia like Russian Federal Security Service (FSB). Cozy Bear is known for a spray and pray spear-phishing campaign that delivers payloads such as Microsoft Word containing malicious macros that launch a PowerDuke backdoor. This allows for a smash and grab collection and exfiltration of specific file types of interest. If the compromised target is of interest to Cozy Bear, they will look to install toolkit like Meterpreter to explore and compromise the target network furthermore.
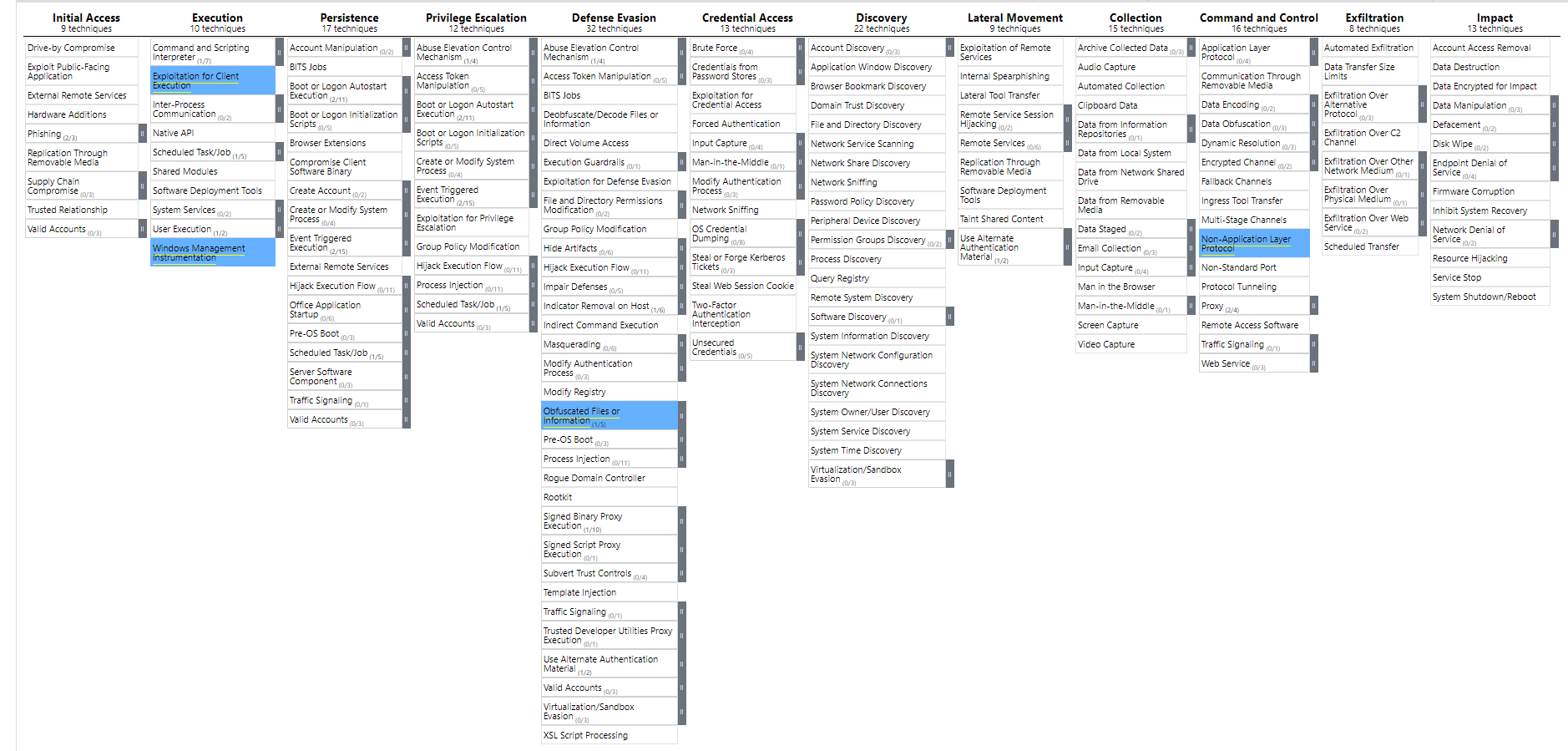
China
What about the great land of Pandas and Chinese cuisines? Well, there has a lot of case of Chinese APT groups attacking Japan over the years so let's start the list:
APT17 also known as Deputy Dog by FireEye security vendor has been documented performing regional software exploitation while targeting Japanese government agencies and other key organisations like education organizations over the past few years with the most recent activity being in spring of 2019. Based on previous attacks, APT17 has the same endgame of delivering the PlugX remote access trojan to allow them to have collected and steal information like intellectual property. The main method of attack from APT17 is to leverage zero-day exploits (CVE-2014-0810 and CVE-2014-7247) found in the regional software like Sanshiro and Ichitaro before spreading malicious documents attached to spear-phishing emails. Then whenever one of the phishing emails was successful, the user would unknowingly allow for the RAT to be delivered while the user opens and reads the malicious file.
Another APT that has been known to leverage zero-day exploits found in the regional software is Bronze Butler. Their typical attack method was to use spear-phishing as the entry point to their target. The malicious attachments were aimed to exploit vulnerabilities in Ichitaro and SkySea Client View. Their typical style of phishing emails was based around themes like disaster prevention. This is a good case of media targeting as at the time, Japan was testing many of its disaster measures which were being discussed in the media. (for more about APT/cyber-criminal groups using media targeting, look at Dougie Grant's talk on the Role of NCSC in the UK.)
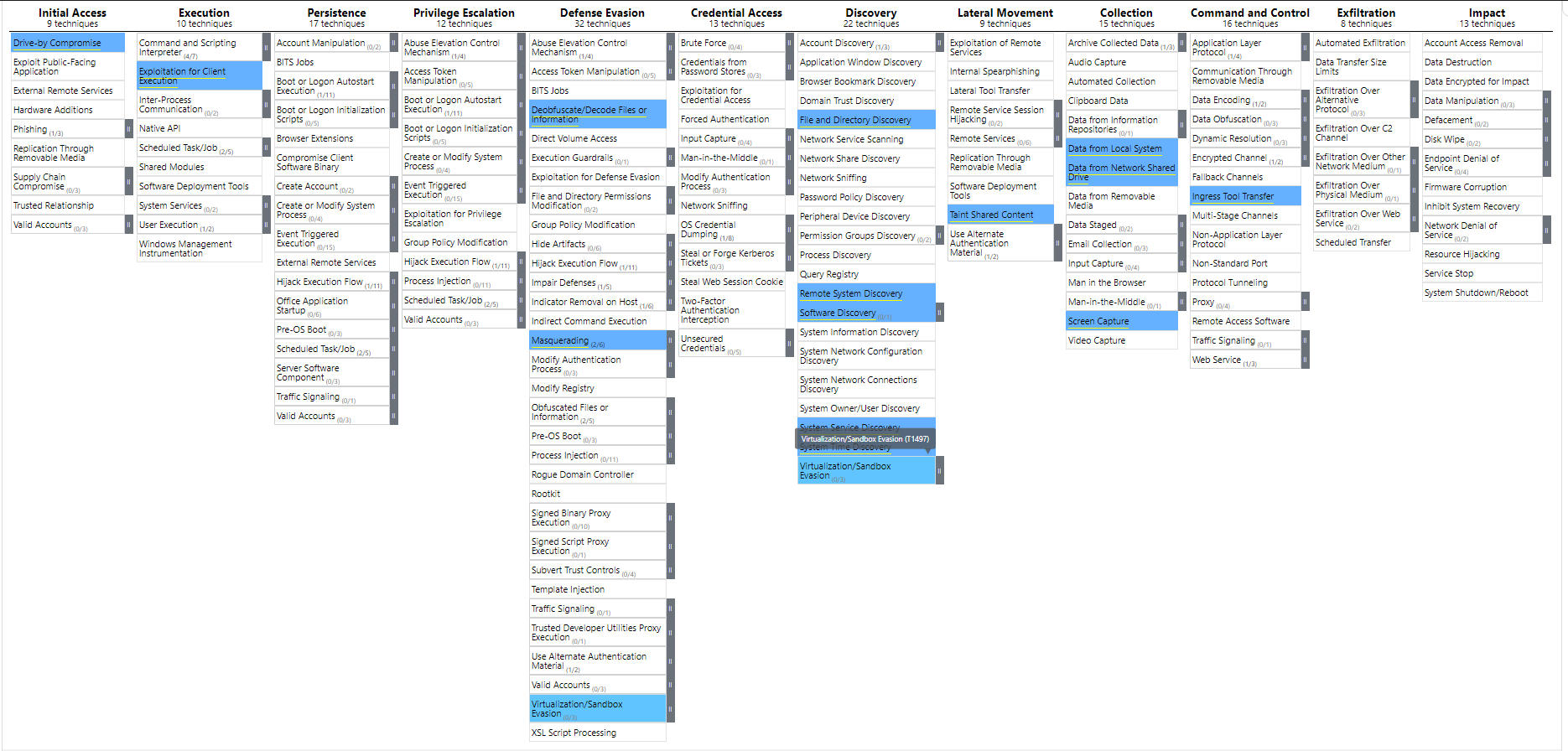
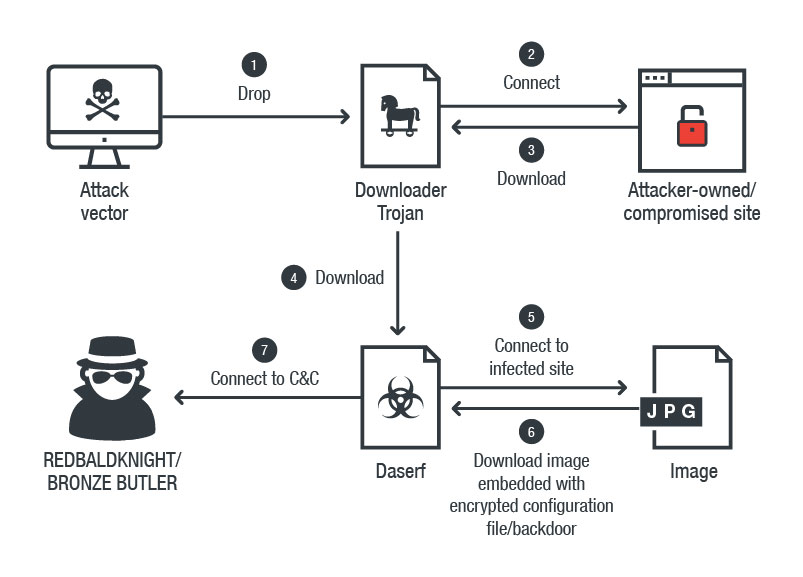
A downloader trojan would be installed on their victim’s machine from malicious attachment and would retrieve a backdoor (Daserf) from a compromised site by Bronze Butler before the backdoor would be used to download an image from another compromised site. Then they would use steganography to hide and extract encrypted data which would be the backdoor configurations or another hacking tool for future use. After the data was decrypted, the backdoor would connect to a C&C (Command and Control) server for further commands.
The Chinese APT groups aren't only using regional software vulnerabilities, Numbered Panda (APT12) have been known to use popular vulnerabilities like CVE-2012-0158. They are believed to be a cyberespionage group that have links to the Chinese People's Liberation Army. Their first major activity was in October 2012, where they compromised the New York Times with the RIPTIDE backdoor but they changed malware family to HIGHTIDE and WATERSPOUT to reduce the chance of them being detected over the years. Eventually, on August 25, 2014, they were observed spear-phishing a high-technology company in Japan where they had attached a malicious document that was designed to exploit CVE-2012-0158.
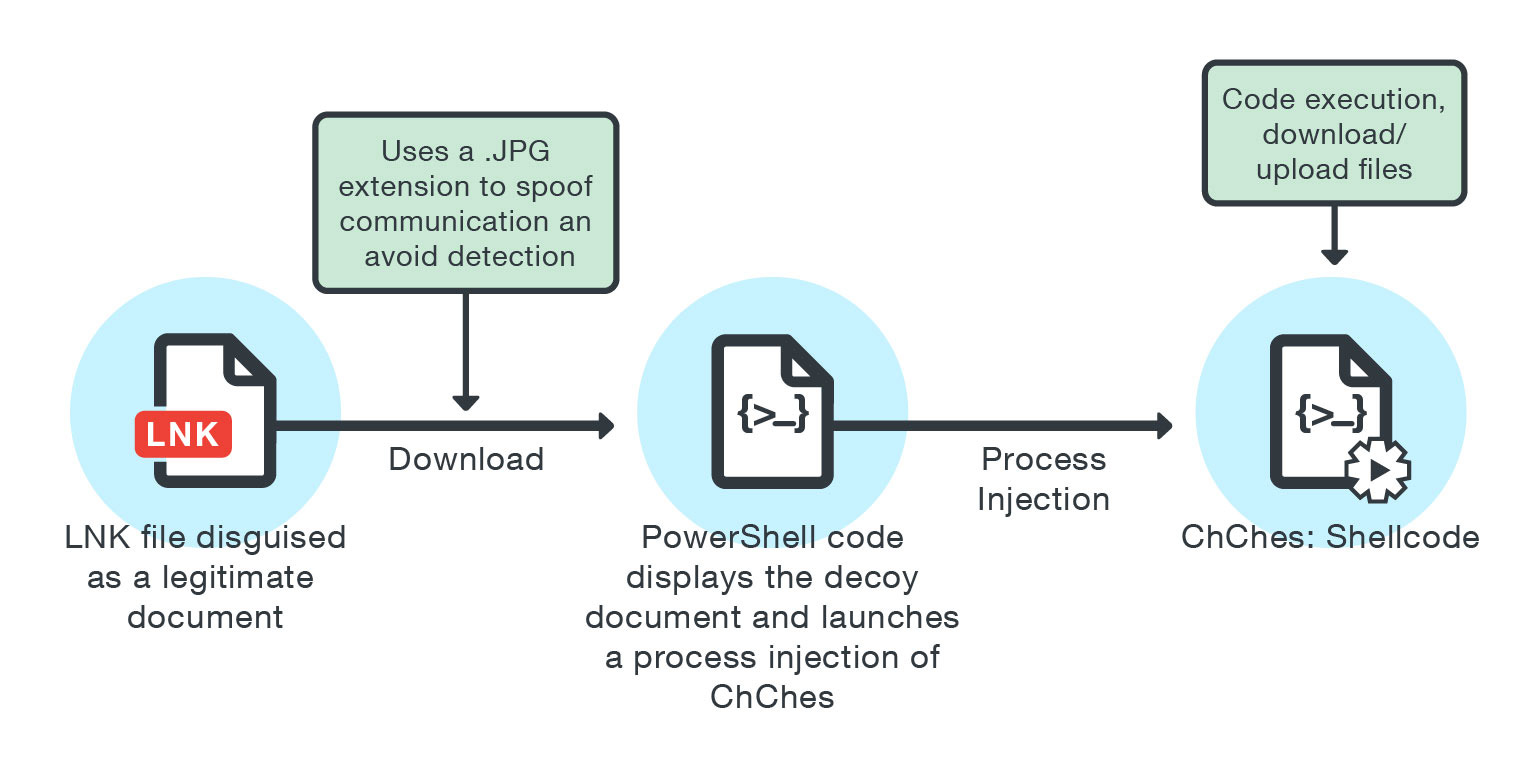
So now for the big boy, Stone Panda (APT10) have been tracked by multiple cybersecurity organisations for years (first documented in 2009). They are known for targeting healthcare, defence, aerospace, and government sectors in the United States, Europe, and Japan to collect military information and steal intellectual property. APT10 follow a similar method of other APT groups of using spear phishing. They leveraged .lnk files with double file extensions (e.g. .JPG) that executes CMD.exe that would download a fake JPG which hides a malicious PowerShell script. A case of this was in September 2016, APT10 targeted Japanese academics where they spoofed several sender email addresses to look like public addresses associated with the Sasakawa Peace Foundation and The White House and used subjects like “[UNCLASSIFIED] The impact of Trump’s victory to Japan,”. The email with that subject was sent two days after the USA election.
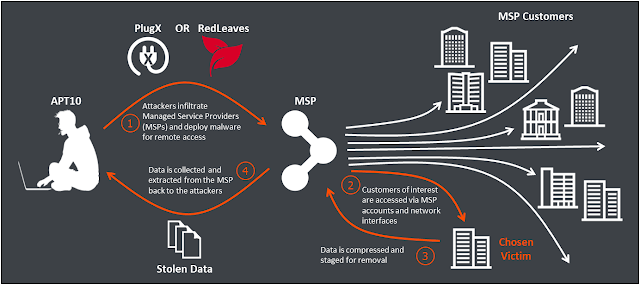
In addition to the spear phishes, APT10 has been documented using Managed Service Providers (MSPs) to access victims. A Managed Service Provider is a third-party company that other companies outsource their day to day management of their IT assets like networks and infrastructure. So, gaining access to MSPs allow for APT10 to have significant access to the MSPs' customer networks. Another positive for ATP10 is web traffic between the MSP and its clients is likely to be seen as harmless so ATP10 can exfiltrate data stealthily and mask their C&C traffic. An example of this that observed by FireEye was an instance involved a SOGU backdoor that was set to communicate with its C&C server through a server belonging to the target’s MSP.
Key Attack!
Cozy Bear
- Office monkeys (2014)
Cozy Bear launched an email campaign attempting to lure victims into clicking on a flash video of office monkeys contained malicious executables.
- Pentagon (August 2015)
Cozy Bear was linked to a spear-phishing cyber-attack against the Pentagon email system causing the shutdown of the entire Joint Staff unclassified email system and Internet access during the investigation of Cozy Bear that was opened after Office monkeys incident.
- Democratic National Committee (2016)
Cozy Bear was discovered in DNC servers and network at the same time as Fancy Bear had carried out spear-phishing campaigns on email addresses associated with the Democratic National Committee which ended up with them gaining access to DNC servers.
- The US think tanks and NGOs (2016)
Cozy Bear was linked to a series of coordinated and well-planned spear-phishing campaigns against U.S.-based think tanks and non-governmental organizations.
- Norwegian Government (2017)
The Norwegian Police Security Service reported that attempts had been made to spear phish the email accounts of nine individuals in the Ministry of Defence, Ministry of Foreign Affairs, and the Labour Party by Cozy Bear.
- Dutch ministries (2017)
The General Intelligence and Security Service (AIVD) of the Netherlands revealed that Fancy Bear and Cozy Bear had made several attempts to hack into Dutch ministries, over a six-month period.
- Operation Ghost (2019)
There was a belief that Cozy Bear had stopped its operation until it was later discovered that they had developed new tools: PolyglotDuke, RegDuke and FatDuke.
- COVID-19 vaccine data (2020)
Cozy Bear was accused of trying to steal data on vaccines and treatments for COVID-19 that being developed in the UK, US, and Canada.
Fancy Bear
- Attacks on journalists (2014-2017):
Fancy Bear targeted numerous journalists in the United States, Ukraine, Russia, Moldova, the Baltics, and other countries who had written articles about Vladimir Putin and the Kremlin.
- German attacks (2014-2015):
Fancy Bear attacked the German parliament for six continuous months and was reportedly targeting the "informationsverbund Berlin-Bonn” (IVBB) network.
- U.S. military wives' death threats (February 10, 2015)
Five wives of U.S. military personnel received death threats that originally was believed to be from a hacker group calling itself "CyberCaliphate", claiming to be an Islamic State affiliate, but later debunked when the victims' email addresses were found to have been in the Fancy Bear phishing target list.
- French television hack (April 2015)
French television network TV5Monde fell victim to an attack by a hacker group calling itself "CyberCaliphate" and claiming to have ties to the terrorist organization Islamic State of Iraq. But this was discounted when evidence was found of APT28 being involved.
- EFF spoof, White House and NATO attack (August 2015):
Fancy Bear used spear-phishing attack with a link to electronicfrontierfoundation.org that was a malicious domain that contained a Java applet with the zero-day exploit of Java (CVE-2015-2590). It was then launched at the White House and NATO.
- World Anti-Doping Agency (August 2016)
The World Anti-Doping Agency reported cases of phishing emails sent to users of its database that claimed to be official WADA communications requesting their login details. But after some reviews, evidence founded pointed to APT28 being responsible for the phishing campaigns.
- Dutch Safety Board and Bellingcat (2016)
Journalists from Bellingcat and the Dutch Safety Board were targeted by multiple spear-phishing campaigns.
- Democratic National Committee (2016)
Fancy Bear carried out spear-phishing campaigns on email addresses associated with the Democratic National Committee which ended up with them gaining access to DNC servers. It is also discovered that Cozy Bear had gained access to the DNC servers and network.
- Ukrainian artillery (2014-2016)
CrowdStrike claimed that APT 28 had targeted the Ukrainian Army's Rocket Forces and Artillery with an infected version of an Android app that controlled the targeting data for the D-30 Howitzer artillery.
- Windows zero-day (October 2016)
Google's Threat Analysis Group revealed a zero-day vulnerability in most Microsoft Windows versions that Fancy Bear had been using in spear-phishing attacks.
- Dutch ministries (February 2017)
The General Intelligence and Security Service (AIVD) of the Netherlands revealed that Fancy Bear and Cozy Bear had made several attempts to hack into Dutch ministries, over a six-month period.
- IAAF hack (February 2017)
The officials of the International Association of Athletics Federations (IAAF) revealed that its servers had been hacked by Fancy Bear.
- German and French elections (2016–2017)
Fancy Bear attempted to phish German and French election campaigns so they could install malware on their sites.
- International Olympic Committee (2018)
Fancy Bear released emails from IOC that retaliation for IOC banning Russian athletes from the 2018 Winter Olympics. But there were concerns that parts of the emails were fake.
- Swedish Sports Confederation (2018)
The Swedish Sports Confederation reported Fancy Bear was responsible for an attack on its network to target records of athletes' doping tests.
- United States conservative groups (2018)
Microsoft reported that Fancy Bear had attempted to steal data from political organizations such as the International Republican Institute and the Hudson Institute think tanks.
- The Ecumenical Patriarchate and other clergies (August 2018)
A report was released stating Fancy Bear had been targeting the email correspondence of the officials of the Ecumenical Patriarchate of Constantinople headed by the Ecumenical Patriarch Bartholomew I for years.
- 2019 think tank attacks (2019)
Microsoft announced that it had detected spear-phishing attacks from APT28, aimed at employees of the German Marshall Fund, Aspen Institute Germany, and the German Council on Foreign Relations.
Lazarus
- Operation Troy (2009)
A DDoS attack was launched by Lazarus against US and South Korean websites that stuck three dozen websites.
- South Korea Cyberattack (2013)
"Ten Days of Rain" attack was a DDoS attack that targeted South Korean media, financial, and critical infrastructure sector that was continued with the "DarkSeoul" wiper attack.
- Sony breach (2014)
Large amounts of data were stolen and leaked. The data leaked included unreleased films, emails, and personal information of employees.
- WannaCry Attack (2017)
The WannaCry Ransomware was released and infected about 230,000 computers globally. It resulted in a third of NHS hospital trusts were affected by the attack.
- Cryptocurrency attacks (2017-2019)
Lazarus was responsible for multiple Cryptocurrency exchange attacks including some Japanese Cryptocurrency exchanges.
Stone Panda
- Operation Cloud Hopper (2014-2017)
Operation Cloud Hopper was an attack on MSPs in multiple countries around the world (e.g. the United Kingdom, United States, Japan, Canada). The goal of this attack was to access systems so they could steal data from the MSPs' clients.
- 2016 US Navy personnel data
Stone Panda accessed records relating to 130,000 US Navy personnel. It was believed that Stone Panda was able to SQL inject the Navy's public-facing website that allowed them to gain access to the database.
Conclusion:
The prime question is do I know anything about these groups? or have I just search it all up? Well, I tell you this, I have been looking into most of these APT groups and more for about a year now. That doesn't mean I know everything about them but I know enough to be concerned and curious about these groups. And the cherry on top of this is I have worked on an attack from one of these groups in real-time as the attack occurs. And looking at how the future is going, it is only the beginning of my experience with these groups. For anyone who is wondering what these groups are doing right now, I can tell you they aren't asleep, especially China.
Now I could have added even more to this blog like case studies but this blog is quite long and I think it's a good first taste of what everyone is in for in terms of my security blogs about Japan. So, it is time to say a big thank you to everyone reading this week's blog. In terms of next week, I will be doing Japanese 101: Essentials word and phrases. (there might be part one and two depending on how the first draft is). So, until next week, arigatou gozaimasu and sayōnara!
