Do you know the basics? Japanese Cybersecurity Laws
The first thing I was taught when dealing with organisations was they always care about two things: profit and laws. When either of these is left unchecked, any organisation can be crippled and even completely shut down.

The first thing I was taught when dealing with organisations was they always care about two things: profit and laws. When either of these is left unchecked, any organisation can be crippled and even completely shut down. So as a cybersecurity student and professional, cybersecurity and data laws are a must when doing any form of work, essay or report. Therefore with my interests around Japan and it's cybersecurity scene, I have spent a decent amount of time reading and trying to understand Japan's cybersecurity and data laws so I can assist Japanese organisations from a wide range of sectors.
Let's start with the basics
The main cybersecurity law in Japan is The Basic Act on Cybersecurity 2014, which was the first dedicated cybersecurity law between the G7 nations (Canada, France, Germany, Italy, Japan, the United Kingdom, and the United States). I first came across it in the summer of 2019 when I saw "Cybersecurity strategy in Japan" report from Japan's national center of incident readiness and strategy for cybersecurity (NISC) which was looking at the present situation and challenges that Japan was facing. One of the key parts of the law is its definition of "Cybersecurity".
"The term "Cybersecurity" means the necessary measures that are needed to be taken to safely manage information, such as prevention against the leak, disappearance, or damage of information which is stored, sent, in transmission, or received by electronic, magnetic, or other means unrecognizable by natural perceptive functions (hereinafter in this section referred to as "Electronic or Magnetic Means"); and to guarantee the safety and reliability of information systems and information and telecommunications networks (including necessary preventive measures against malicious activities toward electronic computers through information network or storage media for information created by electronic or magnetic means (hereinafter referred to as "Electronic or Magnetic Storage Media")), and that those states are appropriately maintained" (Source: The Basic Act on Cybersecurity, Law number: Act No. 104 of 2014)
By defining the term in a legal context, it makes it clearer for everyone when it comes to lawsuits and insurance. The only "issue" with this definition is what does necessary measures mean? Because in my opinion, it varies between cases and threats. You could argue that it should be enough to counter the highest level threats like APT groups/Nation Sponsored groups but not everyone needs to fight off Fancy Bear or Stone Panda. So what is the purpose of the law?
The goal of the law is to help promote cybersecurity nationally by setting forth the basic principles of the national cybersecurity policy and clarifying the responsibilities of the national government, local governments, and other concerned public parties while enhancing the development of an economic society where people can live with a sense of safety and security and contributes to the protection of international peace and security as well as national security. It also set up a baseline for future cybersecurity-related policies such as the cybersecurity strategy formulation and also requires a Cybersecurity Strategic Headquarters to be established.
The laws set out 6 clear principles that allow for the law to work without negatively affecting society. Instead of copying and paste a load of text, I thought I would try to sum up what each principle does:
- Ensuring a free flow of information and the development of economic and social vitality by maintaining the Internet and other advanced information and telecommunications networks where the promotion of the cybersecurity policy is carried out to produce active responses to threats against cybersecurity through coordination among multiple stakeholders, including the national government, local governments, and critical information infrastructure CII Operators.
- The promotion must have the goal of raising awareness to each member of the public about cybersecurity and encourage each member of the public to take voluntary actions to prevent any damage caused by threats against cybersecurity and to positively promote actions to establish resilient systems which can quickly recover from damage or failure.
- The promotion of cybersecurity must proactively be carried out with the intent to implement on maintaining the Internet and other advanced information, telecommunications networks and actions toward the establishment of a vital economy and society through the utilization of information and telecommunications technologies.
- The promotion must have the intent to play a leading role in an internationally-coordinated effort for the creation and development of an international normative framework for cybersecurity.
- The promotion of the cybersecurity policy must be required to be carried out in consideration of the basic principles of the "Basic Act on the Formation of an Advanced Information and Telecommunications Network Society" 2000. (A law with the goal of pursuing "strategies for the formation of an advanced information and telecommunications network society by way of providing basic principles and basic policies for the development of strategies, determining the responsibilities of the government of Japan and local public entities, establishing the Strategic Headquarters for the Promotion of an Advanced Information and Telecommunications Network Society, and providing for the development of a priority policy program on the formation of an advanced information and telecommunications network society, with respect to the formation of an advanced information and telecommunications network society." )
- The promotion of the cybersecurity policy is required to be carried out with due consideration not to wrongfully impinge upon the peoples' rights.
With these principles, it is clear that the Japanese government have a clear end goal of keeping everyone informed of cyber threats and trying to encourage everyone to keep as secure as possible against these threats but as some of you might know from listening to my talk, that end goal is quite far off. Nonetheless, they are working on it, as I also did mention in my talk, so let's take a closer look at what this law means for different parties.
The Government have the responsibility to formulate and implement comprehensive cybersecurity policies that will be promoted across the country.
Local governments have the responsibility to formulate and implement independent cybersecurity policies in consideration of the appropriate division of roles with the national government.
CII (critical information infrastructure) Operators have the responsibility to make an effort to: deepen their awareness and understanding of the critical value of cybersecurity; ensure cybersecurity voluntarily and proactively, and cooperate with the measures on cybersecurity taken by the national government or local governments.
IT/Cybersecurity businesses have the responsibility of making an effort to ensure they voluntarily install cybersecurity measures and proactively keep them up to date. They also are required to cooperate with the measures on cybersecurity taken by the national government or local governments.
Educational and Research Organizations are required to make sure that hey voluntarily install cybersecurity measures and proactively keep them up to date. They also have the responsibility to develop human resources specialized for Cybersecurity, disseminate research and the results of cybersecurity research, and cooperate with measures taken by the national government or local governments.
All of these parties are bound to these responsibilities by Articles 4-8 that lists each parties' responsibilities. So it is clear that the Japanese government have a clear goal of these parties but what about the general public? Well article 9 (The Efforts of the People), states "In accordance with the Basic Principles, the people are to make an effort to deepen their awareness and understanding of the critical value of Cybersecurity and pay necessary attention to ensuring Cybersecurity." which clearly shows that they thought about everyone. So why they are so far from their end goal? Well as much as everyone watching out for themselves is great, their knowledge of new cybersecurity measures and cyber threats will be limited if they don't share information. One of the biggest problems with Japan's cyber scene is the lack of sharing of cybersecurity intelligence as seen in the PwC survey in 2016.
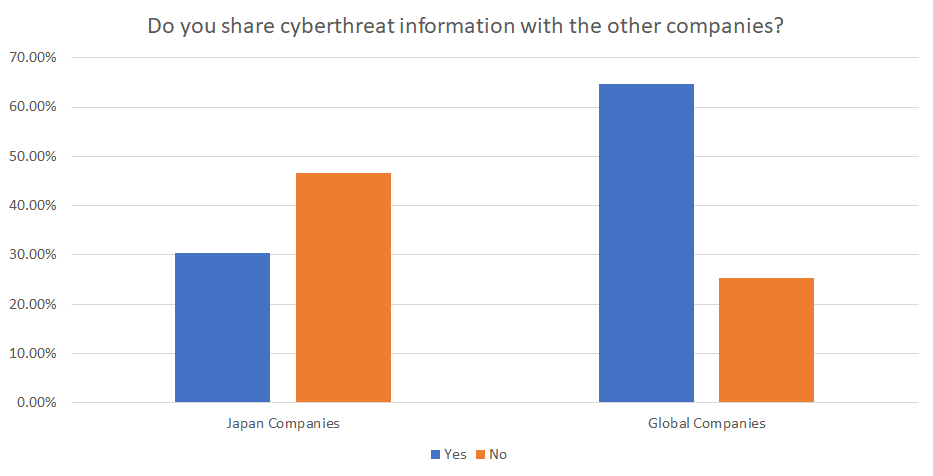
So what could Japan do to fix that? Well as I mentioned in my talk, Japan has set up a cybersecurity council as part of the second amendment of The Basic Act on Cybersecurity. This amendment came about in light of the growing cyberthreats from countries like North Korea who have a very keen interest in Japan. But how does this fix the problem? Well, the purpose of the council is to enhance the information sharing between the members of the council and therefore allows for the promotion of the necessary cybersecurity measures. But there is still the issue of organisations not sharing the information as there is no law that requires them to share the information with the council or their specific information sharing and analysis center (ISAC). So in theory, currently most Japanese companies don't have to report a breach to anyone. There is only one situation where some form of reporting must occur, which when a telecommunication carrier experiences a cyber-attack that causes a serious incident that is specified in the Telecommunication Business Act (The TBA). There are two other situations where reporting is normal but isn't legally required currently, under the Financial Services Agency's (FSA) guidelines for banks, banks are required to report an incident immediately but it isn't legally binding. However, banks nearly always comply as the FSA is a massive and quite powerful regular in the financial sector. The other situation is under the guidelines of the Personal Information Protection Committee (PPC), whenever an incident involves any loss, damage or disclosure of personal information, organisations are expected to submit a summary of the result of the incident and what measures they plan to use to prevent future incidents to the PPC. So it isn't legally binding, but there is an amendment coming soon to the Act on the Protection of Personal Information (APPI), that states all business operator must report any incident to the PPC. So I think it is a good time to move onto some of the other laws that I have mentioned.
Telecommunication Business Act (TBA)
"The purpose of this Act is to ensure that telecommunications services are provided smoothly, and the interests of the users of the services are protected, through making the operation for telecommunications services proper and reasonable and promoting the fair competition in telecommunications business in consideration of the public nature of telecommunications business, thereby ensuring the sound development of telecommunications and the convenience of the lives of the people, and increasing the public welfare." (Telecommunications Business Act Law number: Act No. 86 of 1984)
So what effects does this law have on Japan's cybersecurity scene? Well Article 4 of the TBA states that "the secrecy of communications handled by a telecommunications carrier must not be violated." and "A person who is engaged in telecommunications business must not disclose other persons' secrets which came to their knowledge while in service with respect to communications handled by a telecommunications carrier. The same applies even after that person has left office." so therefore this means any information of any communication like IP addresses and it's contents are protected. But this also caused an issue for telecommunication carrier as they couldn't collect information on possible threat actor communications. However, in 2013, the Ministry of Internal Affairs and Communications (MIC) who are responsible for implementing the TBA, started a project called ACTIVE (Advanced Cyber Threats response InitiatiVE) which aimed to allow for telecom companies to protect internet users from cyberattacks by collaborating with ISPs and vendors of IT systems while following the guidelines that MIC released to address the concerns of the issue with the TBA.
An amendment was made in 2018 (effective since January 2019) to TBC to enable a telecommunications carrier to share with other carriers, the information on transmission sources of cyber-attacks through Japan's ICT-ISAC.
Act on the Protection of Personal Information (APPI)
"This Act aims to protect an individual's rights and interests while considering the utility of personal information including that the proper and effective application of personal information contributes to the creation of new industries and the realization of a vibrant economic society and an enriched quality of life for the people of Japan; by setting forth the overall vision for the proper handling of personal information, creating a governmental basic policy with regard to this, and establishing other matters to serve as a basis for measures to protect personal information, as well as by clarifying the responsibilities etc. of the central and local governments and establishing obligations etc. that a personal information handling business operator shall fulfil, in light of the significantly expanded utilization of personal information as our advanced information- and communication-based society evolves." (Act on the Protection of Personal Information Law number: Act No. 57 of 2003)
This law is quite easy to guess what it is about and what it does. But it also does causes a slight issue around cybersecurity as when organisations are collecting information about cyber-attacks like access logs and sharing it with other organisations, they can be subject to the restriction of the use and disclosure of the data if it includes personal information (unless consent is collected or certain conditions are met).
Act on Prohibition of Unauthorized Computer Access
"The purpose of this Act is to prevent computer-related crimes committed via telecommunications lines and maintain telecommunications-related order as realized by means of Access Control Features by prohibiting acts of unauthorized computer access and stipulating penalties therefor and assistance measures to be taken by Prefectural Public Safety Commissions to prevent the recurrence of such acts, thereby contributing to the sound development of an advanced information and telecommunications society" (Act on Prohibition of Unauthorized Computer Access Act No. 128 of August 13, 1999)
This is another law that is quite easy to guess what it is about and what it does. But what makes it interesting is they set out the very clear prohibition of specific acts unlike UK's Computer Misuse Act 1990 that lists out unauthorised access with specific intents. Unauthorised access in terms of this law refers to spoofing and attacking vulnerabilities, the Access Administrator usually is the main user or the organisation and Access Control Feature is the security feature (login via username and password, 2FA, etc) that control the access of a system or a location in the system. Also, files and data sets are referred to as electronic or magnetic records.
- Prohibition of Acts of Unauthorized Computer Access (Article 3)
- Prohibition of Acts of Obtaining Someone Else's Identification Code (Article 4): It is prohibited for any person to obtain someone else's identification code associated with an Access Control Feature to engage in an Act of Unauthorized Computer Access
- Prohibition of Acts of Facilitating Unauthorized Computer Access (Article 5): It is prohibited for any person, unless there are justifiable grounds for refusing to do so or any other legitimate reason therefor, to supply someone else's identification code associated with an Access Control Feature to a person other than the Access Administrator associated with the Access Control Feature concerned and the Authorized User to whom the identification code concerned belongs.
- Prohibition of Acts of Wrongfully Storing Someone Else's Identification Code (Article 6): It is prohibited for any person to store someone else's identification code associated with an Access Control Feature that has been wrongfully obtained to engage in an Act of Unauthorized Computer Access.
- Prohibition of Acts of Illicitly Requesting the Input of Identification Codes (Article 7): It is prohibited for any person to engage in any of the acts listed below by impersonating an Access Administrator who has added an Access Control Feature to a Specified Computer or otherwise creating a false impression of being the Access Administrator concerned.
In my opinion, what is interesting about this law, is the impact it can have on social engineering. Articles 4, and 6 would mean if I shoulder surfed you, I would be breaking the law. That is an obvious thing but I find it fascinating that this law doesn't care what kind of intent you have as long as it is malicious.
Now, this is where the Criminal (Penal) Code comes in. For those who haven't read my "Who put ice cream in the post-box? A scoop of Japanese laws." blog post, the Penal Code is one of the roppo that makes up modern Japanese law. In this case, the Penal Code sets out the penalties for breaking the law.
- Any person who has violated the provisions of Article 3 shall be punished by imprisonment with work for not more than three years or a fine of not more than 1 million yen. (Article 11)
- Any person who falls under any of the following items shall be punished by imprisonment with work for not more than one year or a fine of not more than 500,000 yen. (Article 12)
- (i): A person who has violated the provisions of Article 4
- (ii): A person who has supplied the identification code of another person in violation of the provisions of Article 5 despite knowing that the recipient intends to use it for an Act of Unauthorized Computer Access
- (iii): A person who has violated the provisions of Article 6
- (iv): A person who has violated the provisions of Article 7
- (v): A person who has violated the provisions of paragraph (3) of Article 9
- Any person who has violated the provisions of Article 5 (excluding a person specified in item (ii)) shall be punished by a fine of not more than 300,000 yen. (Article 13)
Penal code
As the Penal Code is the document lists all the general crimes, it is referenced often in the case of cybercrimes. So here are all the key articles that apply to cybercrime:
- Unauthorised creation of electronic or magnetic records (article 161-2): This law states a person who creates an electromagnetic record which is for use in such improper administration and is related to rights, duties or certification of facts or who has the intent to bring about improper administration of the matters of another person, shall be punished by imprisonment with work for not more than 5 years or a fine of not more than 500,000 yen. The punishment increases to imprisonment with work for not more than 10 years or a fine of not more than 1,000,000 yen when the electromagnetic record to be created by a public office or a public officer.
- Obstruction of business by damaging a computer (article 234-2): This law states a person who obstructs the business of another by interfering with the operation of a computer utilized for the business of the other or by causing such computer to operate counter to the purpose of such utilization by damaging such computer or any electromagnetic record used by such computer, by inputting false data or giving unauthorized commands or by any other means, shall be punished by imprisonment with work for not more than 5 years or a fine of not more than 1,000,000 yen.
- Computer fraud (article 246-2): This law states that a person who defrauds another of property by creating a false electromagnetic record, or inputting false data or giving unauthorized commands shall be punished by imprisonment with work for not more than 10 years.
- Damage of documents for government use (articles 258): This law states that a person who damages a document or an electromagnetic record in use by a public office shall be punished by imprisonment with work for not less than 3 months but not more than 7 years.
- Damage of documents for private use (articles 259): This law states that a person who damages a document or electromagnetic record of another that concerns rights or duties shall be punished by imprisonment with work for not more than 5 years.
- Possession of payment cards with unauthorised electromagnetic records (article 163-3): This law states a person who possesses the unauthorised card, shall be punished by imprisonment with work for not more than 5 years or a fine of not more than 500,000 yen.
- Preparation for unauthorised creation of electromagnetic records of payment cards (article 163-4): This law states that if a person prepares to obtain information or provides information for the creation of a financial electromagnetic record shall be punished by imprisonment with work for not more than 3 years or a fine of not more than 500,000 yen.
- Making of Electronic or Magnetic Records Containing Unauthorized Commands (Article 168-2): This law states that a person who creates or provides any electronic or magnetic records to use them for executing commands on another person's computer without legitimate grounds, shall be punished by imprisonment for not more than 3 years or a fine of not more than 500,000 yen:
- Acquisition of Electronic or Magnetic Records Containing Unauthorized Commands (Article 168-3): This law states a person who acquires or stores records including electronic or magnetic records shall be punished by imprisonment for not more than 2 years or a fine of not more than 300,000 yen.
These articles are key as they cover a lot of the issues that cybersecurity professionals face when dealing with an incident/cases of cybercrime. Some of these articles are clear on what they aimed at like the article 246-2 that is about computer fraud, or articles 163-3 and 163-4 which is about being in possession of stolen card/payment details and creating fake cards from stolen card details (e.g. from card skimming). The ones that might be less clear to some are the last two, articles 168-2 and 168-3 which is about malware (viruses, worms, trojans, etc).
Conclusion:
Overall, the laws and regulations that are in place cover most of the cybersecurity industry from data protection to hacking. But, there are a lot of loopholes in these laws like the fact that a lot of Japanese companies don't report breaches for weeks if not months as there isn't really a law like GDPR that forces them to report incidents in a specific time period. Now changes are being made to fix these loopholes and the loopholes aren't the only reason for the issues they allow for, e.g. victim shaming and the culture around failure is other reasons for companies not reporting incidents for ages. Could I make a talk from this blog? Well, I have a plan to do Tokyo Takedown 2 with some of the contents from this blog.
So, it is time to say a big thank you to everyone reading this week's blog. In terms of next week, I am planning to do a blog on Christmas in Japan. I know this might be a bit annoying but here is the link to the google form for my Q&A blog: https://forms.gle/nbhG8HMW9JQSQVeR9 So, until next week, arigatou gozaimasu and sayōnara!
